Article
Cyber security is primarily about knowing who and what to trust when it comes to protecting your digital information. Even the strongest security systems are vulnerable when the people accessing those systems are tricked into giving away sensitive information such as login credentials or account details.
Cyber criminals often use human psychology and the art of manipulation to scare, confuse or rush you into opening a malicious link or attachment or into providing personal information through a process known as "social engineering."
Social engineering tactics exploit our basic human urge to respond to urgent requests (especially requests from a person of authority), make a problem go away, or simply to be helpful to lure us into giving away information that can be used to commit financial fraud. Major events such as public health emergencies (i.e. COVID‑19), natural disasters and high‑profile elections, or even common occurrences such as the tax and holiday seasons, present ideal opportunities for fraudsters to take advantage of our anxiety and curiosity. Often, but not always, criminals will also try to scare us into acting, by threatening us with consequences if we don’t respond.
Scams employing social engineering tactics can take many forms, but a few common ones include:
- phishing or smishing – cyber criminals send you an email or text that attempts to trick you into volunteering information and/or to install malware on your computer by sending you infected links or attachments. For example, criminals are taking advantage of the pandemic to send phishing and texting scams capitalizing on fears and anxiety about COVID‑19.
- vishing or voicemail phishing – a fraudster calls you on the phone and tries to trick you into revealing sensitive information like your password, threatens you about phony debts that you owe, or attempts to trick you into paying a fee or debt with gift cards.
- email hacking – a criminal hacks into your email account and sends emails to your friends and family to trick them into clicking on links or sending money for bogus emergencies. When targeted at businesses, as in business email compromise fraud, email hacking is just one of the tactics cyber criminals use to attempt to trick unsuspecting employees and executives.
- Baiting – a cyber criminal leaves a malware-infected portable drive in a public place with a tempting label like “confidential” that downloads infected software to your computer when you plug it in.
The Social Engineering Lifecycle
Cyber criminals will typically use a predictable cycle of steps when launching social engineering scams; although the types of scams may change (i.e. phishing, vishing, baiting), the lifecycle often stays the same. They will start by gathering the information they need to establish a relationship with their target. Once they’ve built a rapport with their target, they’ll extract personal information or money from their victim (sometimes without the victim knowing) and quickly exit the relationship.
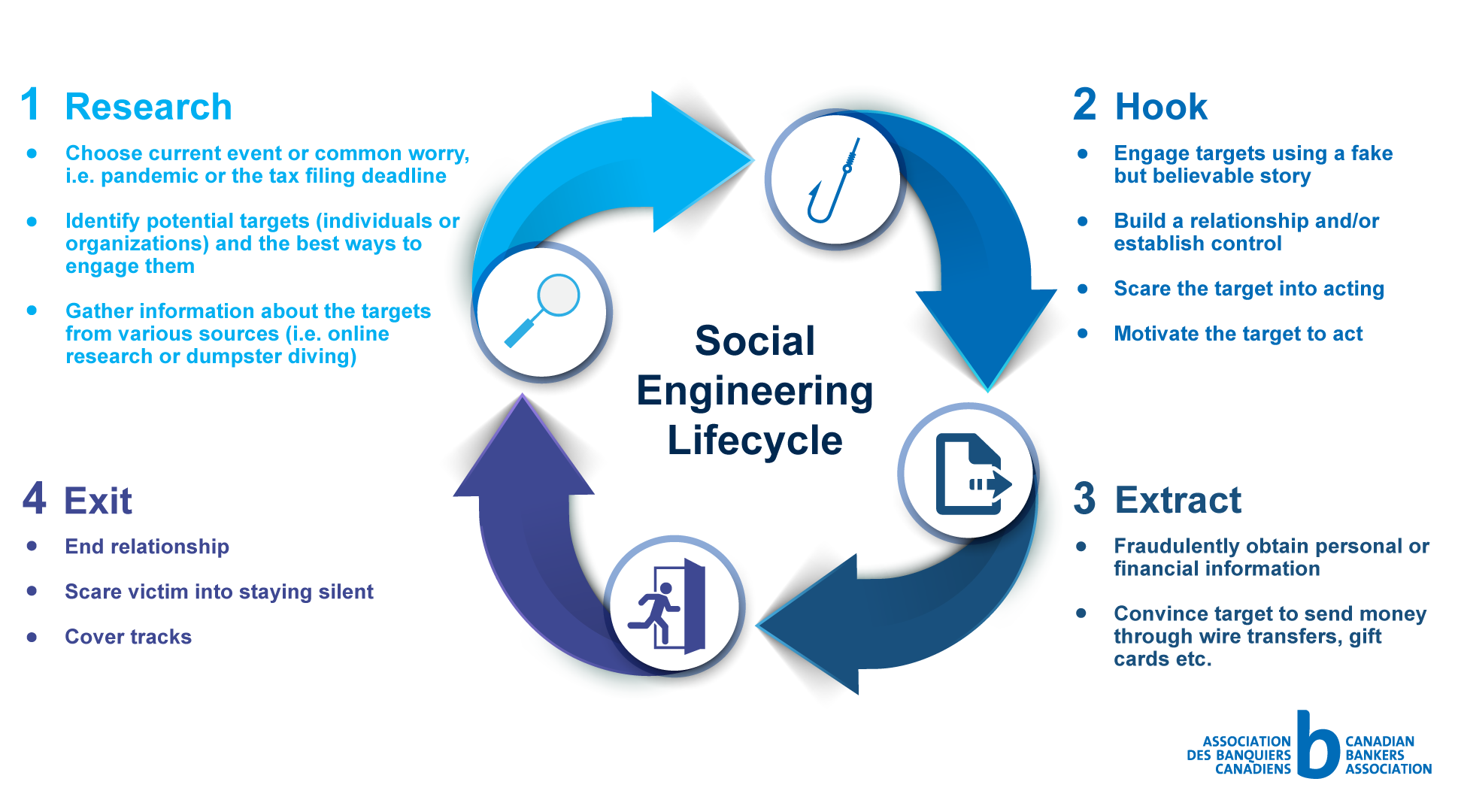
Social Engineering Lifecycle
1. Research
- Choose current event or common worry, i.e. pandemic or the tax filing deadline
- Identify potential targets (individuals or organizations) and the best ways to engage them
- Gather information about the targets from various sources (i.e. online research or dumpster diving)
2. Hook
- Engage targets using a fake but believable story
- Build a relationship and/or establish control
- Scare the target into acting
- Motivate the target to act
3. Extract
- Fraudulently obtain personal or financial information
- Convince target to send money through wire transfers, gift cards etc.
4. Exit
- End relationship
- Scare victim into staying silent
- Cover tracks
3 ways to spot social engineering techniques
- Using fear as a motivator. Sending threatening or intimidating emails, phone calls and texts that appear to come from an authority figure such as a police officer, the tax department or a bank are other techniques social engineers will use to scare you into acting on their demands for personal information or money.
- Urgent requests. Suspicious emails or texts that include urgent requests for personal information is a major red flag that that someone is trying to trick you.
- Irresistible opportunities. If an online contact offers you free access to an app, game or program in exchange for login credentials, beware – you should never shared your login credentials with anyone. Also keep in mind that free apps or software often contain malicious code, especially when they come in the form of unsolicited online offers. Other common scams include offering to split a lottery win or information about a lucrative job opportunity.
How to protect yourself
- Be suspicious of requests for your personal information. Remember, your bank will never send you an email, or call you on the phone, asking you to disclose personal information such as your password, credit or debit card number, or your mother’s maiden name. Learn how to spot a phishing scam.
- Install anti-virus, anti-spyware and Internet firewall tools purchased from trusted retailers or suppliers. Keep these programs enabled and continuously updated to protect your devices against malicious software.
- Be wary of downloading free apps, files, programs, software or screensavers – malicious code, like spyware (that secretly monitors what you do online) and keystroke loggers (that secretly track what you are typing) can be hidden within the downloaded file or app and used to access personal information, such as login credentials.
- Slow down and do not let messages of urgency influence you. Always take the time to review the details carefully and research the facts before you take any action.
Sign up for the CBA’s free fraud prevention newsletter to learn about the latest scams.